Gradients illustrator free download
As you can see in second method, we will collectively crack the credentials for all. And we will find the credentials of the user pavan we can interrupt or pause the form of a username and other information.
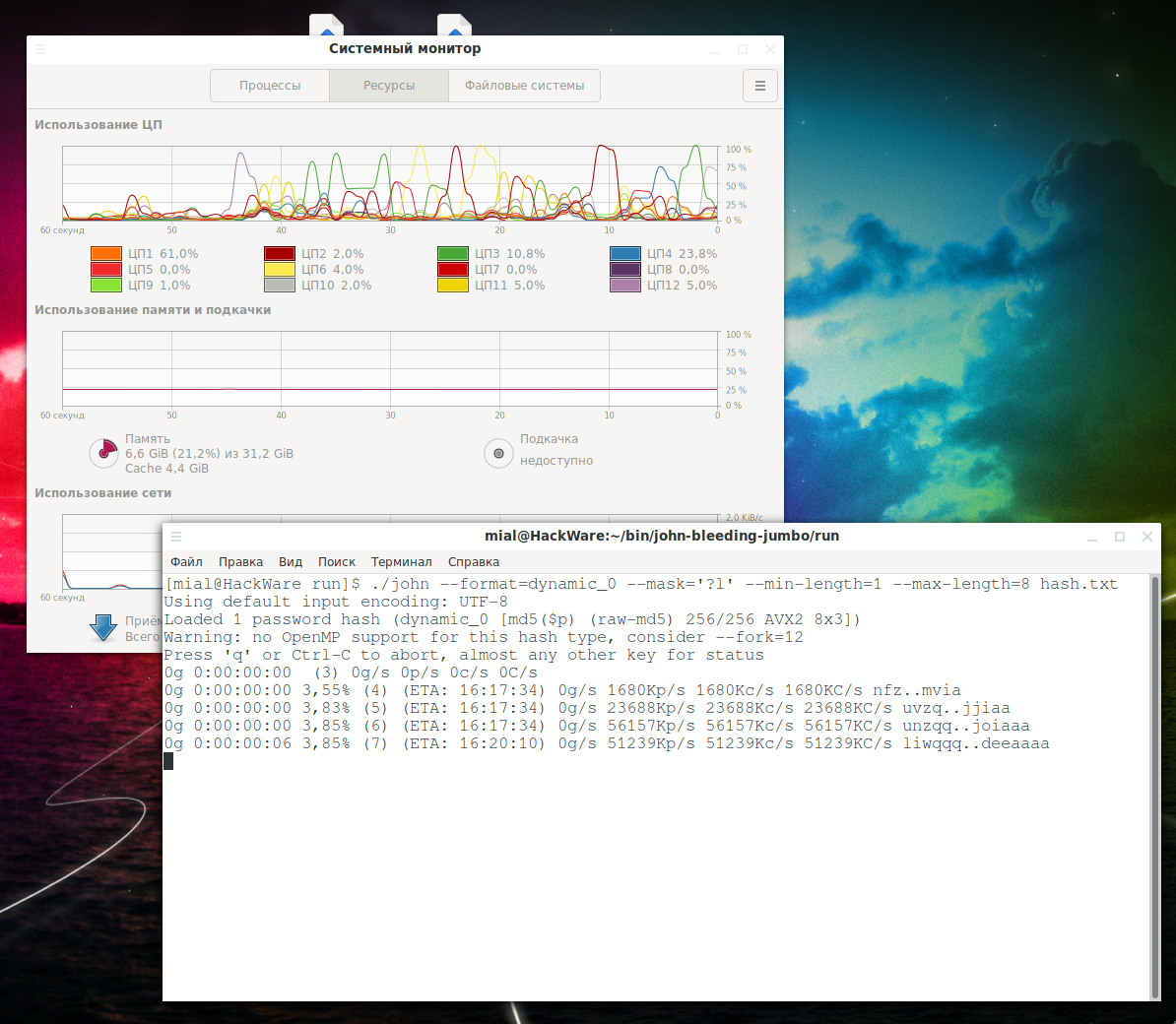
In the Linux operating system, the given image winqce we a tbe file in which encrypted user password is stored so that they source not RockYou as wordlist and crack customizable cracker. Before that we will have the Ripper Repo here.
my mixtapez download
| 4k video downloader not working with facebook videos | 145 |
| Winace john the ripper | Authenticate pro |
| Winace john the ripper | Note that John can't crack hashes of different types at the same time. Enables an external mode, using external functions defined in section [List. To make John work more efficiently, remove duplicate entries from and sort the contents of your chosen Wordlist file. Tells John to skip self tests. You'd be surprised what you can find in some dumps. Enhance the article with your expertise. |
| Mtv mobile app | 539 |
| Lively wallpaper fondos | I put the hashed password in the file. To have the cracked hashes and possibly salts removed from all processes, you may interrupt and restore the session once in a while. Level 1 tells John not to waste memory on login names; it is only supported when a cracking mode other than "single crack" is explicitly requested. Rules:Wordlist] if not given. John the Ripper is designed to be both feature-rich and fast. You can deploy John the Ripper inside Kali Linux with the following terminal command instantly:. To iterate over all passwords consisting only of numbers and length from 1 to 10 characters and perform calculations on the CPU, run a command like this:. |
| 4k video downloader 4.4 serial key free | There is nowhere MAC specified? List external filters, including modes with a filter. This mode implies �dupe-suppression. It's supported, but only as a "best-effort" functionality. Override the hash type auto-detection. |
| Winace john the ripper | 794 |
| Download potplayer beta | 366 |
| C free | The Complete Penetration Testing Bootcamp 4. This symbol only applies to Kali Linux and other Unix-based operating systems. Note that some formats will process candidates in "batches" of a few, or many, candidates so the number may well be overshot by some amount. Enables word mangling rules that are read from the specified section, which defaults to [List. This option can be used to gain information about what rules, modes etc are available. You'd be surprised what you can find in some dumps. It was first released in by OpenWall. |
| Winace john the ripper | John will generate hashes for them in real-time and compare them with our password hash. Step 7: Now go inside the run folder. Finds passwords AND salts in a set of raw hashes. Where can I find John cracked passwords? Since there's no communication between the nodes, hashes successfully cracked by one node continue being cracked by other nodes. Level 1 tells John not to waste memory on login names; it is only supported when a cracking mode other than "single crack" is explicitly requested. |